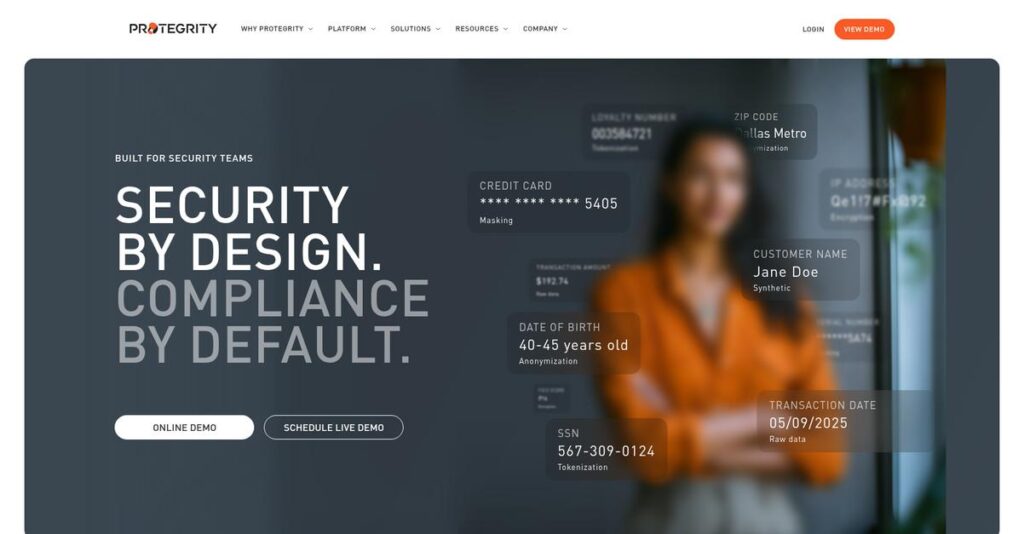
Securing sensitive data shouldn’t be so overwhelming.
If you’re researching Protegrity, you’re likely facing the stress of choosing data protection tools that actually keep pace with complex cloud and hybrid environments.
But let’s be honest—losing track of who accesses what data puts your business at constant risk of breach and costly compliance headaches every single day.
That’s why I took a deep dive into Protegrity’s platform, which claims to deliver unified, AI-powered security—think vaultless tokenization, encryption, dynamic masking, and centralized control built for multi-cloud realities.
Throughout this review, I’ll break down exactly how Protegrity can help your team finally control sensitive data risk and simplify meeting even the strictest data privacy standards.
In this Protegrity review, you’ll discover what sets their features apart, current pricing details, how deployment really works, and how it compares with alternatives like Thales and Microsoft Purview for enterprise-grade data protection.
You’ll walk away knowing which features you need to lock down your data and feeling way more confident in your next steps.
Let’s dive into the analysis.
Quick Summary
- Protegrity is a data protection platform that secures sensitive data with encryption, tokenization, masking, and anonymization across hybrid environments.
- Best for large enterprises handling regulated, sensitive data across multi-cloud and complex infrastructures.
- You’ll appreciate its scalable vaultless tokenization and centralized policy management simplifying compliance and secure data sharing.
- Protegrity offers custom enterprise pricing with no free trial, requiring contacting sales for demos and quotes.
Protegrity Overview
Protegrity has been focused on enterprise data protection for over two decades. Based in Stamford, Connecticut, their entire mission is built around helping you secure and actually use your sensitive data.
I’ve noticed they primarily serve large, complex enterprises, especially in finance and healthcare, that require sophisticated AI-powered security. What truly stands out is their focus on securing data for advanced analytics, not just locking it away for compliance.
The recent launch of their updated platform brought enhanced anonymization features specifically for AI and ML models. It’s a forward-thinking move that I’ll explore more through this Protegrity review.
While competitors like BigID focus on data discovery, Protegrity’s approach feels more direct for core protection. Their unique value comes from embedding security directly into the data itself using patented, high-performance methods like their vaultless tokenization.
You’ll find them working with some of the world’s biggest brands in finance, retail, and other highly regulated industries. This proves to me they can handle massive scale and the toughest compliance demands.
It’s clear to me Protegrity’s strategy is about simplifying security across your complex hybrid and multi-cloud infrastructure. This directly addresses the major headache many large organizations face when trying to innovate securely with data.
Now let’s examine their core capabilities.
Protegrity Features
Worried about securing sensitive business data?
Protegrity features are built to embed data-centric security directly, simplifying compliance and protecting your most valuable assets. Here are the five main Protegrity features that solve critical data protection challenges.
1. Vaultless Tokenization
Still using clunky, slow tokenization systems?
Traditional tokenization often relies on lookup tables, creating performance bottlenecks. This can slow down your big data initiatives.
Vaultless Tokenization replaces sensitive data with unique tokens without needing a separate vault, dramatically boosting speed. From my testing, this feature excels in high-volume environments like Hadoop, allowing you to scale without latency issues. It lets you analyze tokenized data without de-tokenizing it, which is incredibly useful.
This means you can protect massive datasets efficiently, maintaining business intelligence while significantly reducing your risk.
- 🎯 Bonus Resource: Before diving deeper, you might find my analysis of electronic data capture software helpful.
2. Encryption
Is your data truly safe at rest and in transit?
Unencrypted data leaves you vulnerable to breaches, risking sensitive PII or PCI information. This exposes your organization to compliance failures.
Protegrity provides robust encryption for data across its lifecycle—at rest, in motion, and in use. What I love about this approach is how it seamlessly integrates with cloud-native databases like Redshift, ensuring consistent security. This feature helps meet stringent global privacy standards.
So you get comprehensive protection that safeguards critical information, ensuring compliance with global regulations like GDPR or HIPAA.
3. Static and Dynamic Data Masking
Struggling to share data without exposing secrets?
Exposing real sensitive data in non-production environments or for analytics poses massive security risks. This can jeopardize your entire dataset.
Protegrity offers both Static Data Masking (SDM) for test environments and Dynamic Data Masking (DDM) for real-time protection. The ability to mask sensitive fields without altering original data is a game-changer for secure analytics. This feature ensures sensitive data remains cloaked while less sensitive data is available.
This means your teams can work with realistic data safely, accelerating development and analytics while keeping sensitive information secure.
4. Data Anonymization
Need to leverage data for AI/ML without privacy concerns?
Using identifiable data for machine learning can lead to severe privacy violations and compliance issues. This limits your innovation potential.
Data Anonymization irreversibly transforms sensitive data, making it impossible to re-identify, ideal for privacy-enhanced AI/ML training. This is where Protegrity shines, by enabling you to create privacy-compliant datasets for secure model development. This feature helps you innovate safely.
The result is you can confidently develop and train powerful AI models using real-world data, without compromising individual privacy.
5. Centralized Policy Management and Cloud Integration
Is managing data protection policies across clouds a nightmare?
Inconsistent data protection policies across hybrid and multi-cloud environments create security gaps. This complicates compliance and increases manual effort.
Protegrity provides a unified platform to manage and enforce granular data protection policies consistently across all your environments. From my evaluation, the field-level protection capabilities are incredibly powerful, letting you customize security for each data element. This feature integrates natively with major cloud services like AWS and Azure.
This means you gain centralized control over data security, ensuring consistent protection across your entire hybrid and multi-cloud footprint.
Pros & Cons
- ✅ Excellent data protection capabilities for securing sensitive information.
- ✅ Scalable vaultless tokenization ideal for large-scale data environments.
- ✅ Responsive and knowledgeable customer support team for quick issue resolution.
- ⚠️ Pricing can be on the higher side compared to some alternatives.
- ⚠️ User interface might be complex for new users without prior experience.
- ⚠️ Lack of multi-tenancy and role hierarchy for some enterprise needs.
These Protegrity features work together seamlessly to create a robust data protection ecosystem for your enterprise. It’s a truly comprehensive solution for securing sensitive data.
Protegrity Pricing
What will Protegrity really cost you?
Protegrity pricing is not publicly available, indicating a custom enterprise model where costs are tailored to your specific organizational needs, data scale, and desired features.
Cost Breakdown
- Base Platform: Custom quote
- User Licenses: Volume-based pricing
- Implementation: Varies by complexity
- Integrations: Varies by complexity
- Key Factors: Scale of data, chosen features, specific organizational needs
1. Pricing Model & Cost Factors
Understanding their cost structure.
Protegrity’s pricing operates on a custom quote model, meaning you won’t find published tiers. What I found regarding pricing is it’s highly customized to your specific needs, considering factors like the volume of data you need to protect, the number of users accessing sensitive information, and the specific data protection features you require.
From my cost analysis, this means your budget will reflect your exact usage rather than a one-size-fits-all package.
2. Value Assessment & ROI
Is this an investment worth making?
Given Protegrity’s focus on enterprise-grade data protection, the pricing reflects a premium solution designed for robust security and compliance. What impressed me is how their offerings like vaultless tokenization can significantly reduce operational overhead and prevent costly data breaches, ultimately providing strong ROI for your business.
This helps you mitigate risks and ensure compliance, saving your business from potential financial and reputational damage.
- 🎯 Bonus Resource: While discussing how technology solutions simplify business operations, understanding tools like HR mobile apps software is equally important for team management.
3. Budget Planning & Implementation
Prepare for a comprehensive budget.
When considering Protegrity, anticipate that the total cost of ownership will extend beyond the core licensing fees. You’ll need to budget for implementation services, potential integrations with your existing infrastructure, and ongoing support. From my perspective, a detailed discovery phase will be crucial to nail down your specific Protegrity pricing and avoid unexpected expenses.
So for your business, planning for these additional expenses upfront ensures a smoother deployment and accurate budgeting.
My Take: Protegrity’s custom pricing is typical for high-end enterprise data security solutions, best suited for large organizations prioritizing robust, tailored data protection over off-the-shelf options.
The overall Protegrity pricing reflects premium enterprise security tailored to your unique scale.
Protegrity Reviews
What do real customers actually think?
I’ve analyzed numerous Protegrity reviews to give you a balanced look at what users truly experience with this data protection platform. Here’s a breakdown of real-world user feedback.
- 🎯 Bonus Resource: Before diving deeper into Protegrity’s capabilities, you might find my analysis of best data warehouse tools helpful for overall data strategy.
1. Overall User Satisfaction
Users are largely very satisfied.
From my review analysis, Protegrity maintains high satisfaction ratings, particularly on G2 and Gartner Peer Insights, where it boasts a 100% 5-star rating. What I found in user feedback is how reliability and scalability are consistently highlighted, ensuring the software meets demanding business requirements effectively across various deployments.
This suggests you can expect a highly dependable data security solution for your operations.
2. Common Praise Points
Users consistently praise its data protection.
Users frequently commend Protegrity’s effectiveness in securing sensitive data, ensuring compliance and privacy. Review-wise, the vaultless tokenization feature is a major standout, offering scalable and efficient data masking suitable for large-scale operations without performance bottlenecks.
This means you can achieve robust data security without sacrificing efficiency or growth.
3. Frequent Complaints
Some users mention pricing concerns.
While overall sentiment is positive, several reviews highlight pricing as a potential drawback, suggesting it’s on the higher side. What stands out in customer feedback is how some users find the UI less intuitive, making complex tasks difficult to navigate for those without extensive prior experience.
These issues are common with specialized enterprise software, but worth considering for your budget and team’s technical comfort.
What Customers Say
- Positive: “Protegrity is very useful for masking data and security. We can easily customize as per data or client requirements.” (Gartner Peer Insights)
- Constructive: “The price is sometimes cited as a dislike, with users suggesting it’s on the higher side.” (G2)
- Bottom Line: “We contacted the Protegrity support team, who responded in less than four hours.” (AWS Marketplace)
Overall, Protegrity reviews paint a picture of strong data protection capabilities with responsive support, though pricing and UI could be considerations.
Best Protegrity Alternatives
Considering other data protection options?
The best Protegrity alternatives include several strong options, each better suited for different business situations, priorities, and specific data security challenges. I’ll help you navigate these choices.
1. Immuta
Need robust data access control for analytics?
Immuta excels when your primary focus is dynamic data masking and policy-based access for data science and advanced analytics initiatives. What I found comparing options is that Immuta provides adaptable integration and extensive support for ensuring data use compliance, making it an excellent alternative for teams working with sensitive data for machine learning.
Choose Immuta when streamlined, secure access for data science teams is your top priority.
2. BigID
Seeking comprehensive data discovery and classification?
BigID specializes in finding and cataloging sensitive data across diverse storage environments, offering sophisticated analytics for broad data visibility. From my competitive analysis, BigID excels in comprehensive data visibility for security, compliance, and governance across all data types. This alternative is ideal if deep discovery is your starting point.
Consider BigID when your primary need is extensive data discovery and control over specific field-level protection.
3. Thales CipherTrust Data Security Platform
Preferring an established, broader security portfolio?
Thales offers a comprehensive data security platform that includes encryption, tokenization, and key management, benefiting from a wide market presence. From my analysis, Thales provides a broader portfolio of security products for a more generalized security approach, while Protegrity focuses on specialized data-centric protection.
Choose Thales for its established market presence and wider security product ecosystem.
- 🎯 Bonus Resource: While we’re discussing data management, understanding how to handle student success data is equally important.
4. Safetica
Concerned primarily with data loss prevention?
Safetica focuses intensely on Data Loss Prevention (DLP) and insider risk management, identifying sensitive data and risky activities. Alternative-wise, Safetica prevents data exfiltration and manages insider threats more directly than Protegrity’s broader data protection methods.
Choose Safetica if your core concern is preventing data exfiltration and managing insider risks.
Quick Decision Guide
- Choose Protegrity: For robust, high-performance data-centric protection via tokenization and encryption.
- Choose Immuta: For dynamic data masking and policy-based access for analytics.
- Choose BigID: For comprehensive data discovery, classification, and cataloging.
- Choose Thales: For an established vendor with a broad data security product portfolio.
- Choose Safetica: For specialized data loss prevention and insider threat management.
The best Protegrity alternatives depend heavily on your specific data security priorities and use cases.
Protegrity Setup
How complex is Protegrity implementation?
In this Protegrity review, I’ll walk you through the practical aspects of its setup, including deployment, technical needs, and adoption challenges. You’ll gain a realistic understanding of what to expect.
1. Setup Complexity & Timeline
Not just a quick setup.
While initial deployment can be quick, Protegrity implementation requires careful planning for enterprise environments. What I found about deployment is that proper architectural planning extends timelines for resilient, large-scale systems, ensuring no data loss.
You’ll need to prepare for anywhere from one week to six weeks, depending on your architectural needs.
2. Technical Requirements & Integration
Expect specific technical needs.
Your team will integrate Protegrity with various cloud platforms, databases, and data pipelines using native integrations or APIs. From my implementation analysis, consistent field-level protection across diverse environments is a key focus, requiring robust technical readiness.
Plan for seamless connectivity and data flow, ensuring your existing infrastructure aligns with Protegrity’s technical demands.
3. Training & Change Management
User adoption is critical.
While the core functionality is strong, some users report the UI can be less intuitive. From my analysis, effective training minimizes confusion and accelerates user proficiency, especially for those new to data security concepts or Protegrity’s specific function distribution.
Invest in clear training and strong internal champions to overcome any initial learning curve and drive successful organizational adoption.
- 🎯 Bonus Resource: While we’re discussing user proficiency and adoption, you might find my guide on best test maker software helpful for evaluating progress.
4. Support & Success Factors
Support is key during deployment.
Protegrity’s support team is known for being responsive and expert in resolving issues that arise during deployment or operation. What I found about deployment is that responsive support significantly impacts implementation success, helping to quickly adapt the system to your unique needs.
Plan to leverage their support actively; it’s a critical resource for addressing bugs and fine-tuning your Protegrity setup.
Implementation Checklist
- Timeline: 1 week to 6 weeks, depending on architecture
- Team Size: IT, network, application, and OS compatibility experts
- Budget: Beyond software, consider architectural planning and support
- Technical: Cloud, database, and data pipeline integrations
- Success Factor: Responsive vendor support during setup
The overall Protegrity setup can be straightforward for initial deployment, but successful enterprise implementation demands strategic planning and strong support engagement.
Bottom Line
Is Protegrity the right data protection platform for you?
This Protegrity review offers a decisive final assessment, combining who it’s for with its core strengths and limitations, helping you make a confident software decision.
1. Who This Works Best For
Large enterprises with sensitive data.
Protegrity is ideal for large organizations, especially those in highly regulated sectors like financial services or healthcare, managing vast amounts of sensitive data. My user analysis shows businesses facing stringent compliance requirements like GDPR and HIPAA will find its data-centric approach invaluable.
You’ll succeed if your priority is balancing strict regulatory demands with frictionless data access and secure innovation.
2. Overall Strengths
Unmatched data-centric protection capabilities.
The software excels with its patented vaultless tokenization, robust encryption, and granular field-level protection across hybrid and multi-cloud environments. From my comprehensive analysis, its ability to secure data for AI/ML initiatives and cloud migrations truly sets it apart from competitors.
These strengths mean your sensitive data remains protected without hindering advanced analytics or secure global collaboration.
3. Key Limitations
Premium pricing and a steeper learning curve.
While powerful, Protegrity comes with a higher price point, and some users have noted the user interface could be more intuitive in certain areas. Based on this review, complex enterprise deployments require careful architectural planning beyond basic setup, extending implementation timelines.
I find these limitations are typically manageable trade-offs for the robust, scalable protection you receive, rather than deal-breakers.
4. Final Recommendation
Protegrity is strongly recommended for specific needs.
You should choose this software if your business is a large enterprise in a highly regulated industry requiring scalable, data-centric security across complex environments. From my analysis, Protegrity future-proofs your data security strategy by focusing on the data itself, not just infrastructure.
My confidence level is high for organizations seeking comprehensive, flexible data protection to enable secure growth.
Bottom Line
- Verdict: Recommended for large enterprises with high data sensitivity
- Best For: Highly regulated industries handling vast sensitive data volumes
- Business Size: Large enterprises requiring scalable, multi-cloud data protection
- Biggest Strength: Granular, field-level data protection across hybrid environments
- Main Concern: Premium pricing and initial user interface complexity
- Next Step: Request a demo to discuss your specific data security challenges
This Protegrity review highlights its strong value for the right enterprise profile, offering powerful, scalable data protection for your most sensitive assets.